With biometrics YOU are the key
It’s difficult to understand why security is often left on the sidelines of the home automation industry.
Sure, it may not be as ‘sexy’ as a home theatre, but without security your home theatre may not be around for long.
ADVERTISEMENT
It could be the case that people assume security measures are part and parcel of a control system, but with thousands upon thousands of dollars being spent on big-ticket AV products, is it really safe to make such an assumption?
And with everything modern technology is capable of, why can’t security play a ‘sexier’ role in an installation?
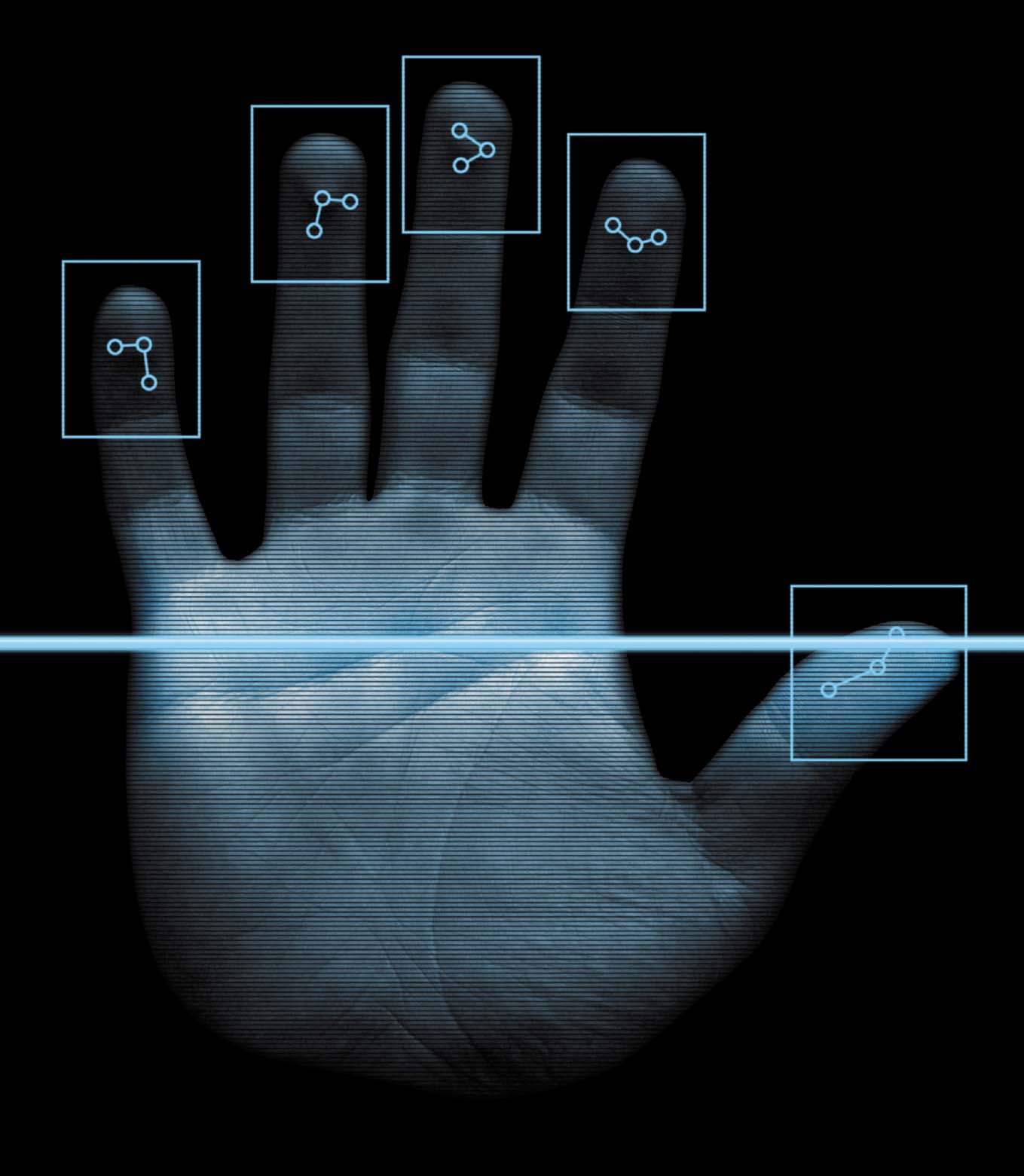
Biometrics are devices that use measurable, physical characteristics or behavioural traits to recognise the identity, or verify the claimed identity, of a person.
These long-time staples of spy novels and movies include fingerprint and retina scans, voice analysis and facial recognition.
“Biometrics is a method of uniquely identifying individuals to allow them access into a property or to disarm a security system,” Central Monitoring Services (CMS) managing director Neville Kiely says.
CMS is a privately owned Australian provider of monitoring services to the security industry and for commercial and domestic security systems.
“The most commonly used biometric systems are hand and finger scans and retina matching. But any part of an individual that is different from another can be used.
“Realistically, DNA would be the ultimate biometric.”
As with most technologies, some people will always take them to the extreme. Australian technology wiz Jonathan Oxer decided to surgically insert a microchip into his left forearm so he would not have to bother with keys (Connected Home Australia May/June, p20).
Jonathan, 37, recently retired as head of the Linux Australia community group. He is now technical director of his own company, Internet Vision Technologies.
His vision is to create a completely automated home reminiscent of those featured in the sci-fi books he grew up with.
“I always realised that I’d be able to find some dodgy backyarder like a tattoo parlour or body-piercer to insert the chip if I really wanted to, but I wanted to avoid that approach,” he says.
“I went to my GP with the chip, an implanting tool and documentation. He was intrigued by the project and referred me to a colleague, a hand surgeon, who he thought might be interested in performing the actual procedure.”
Jonathan originally intended to have the chip implanted in the webbing between his thumb and forefinger so it could be activated by a reader inside a doorknob, allowing him to open locked doors as if they were unlocked. But his forearm was deemed the safer option.
“Despite his interest, the surgeon could not perform the procedure because his medical insurer wouldn’t cover him for any liability associated with it. Medical insurance covers a list of predefined procedures, and implanting an RFID tag into a human isn’t on that list.
“I took it as far as I could with having the process performed by a surgeon, but ultimately it just was not possible. In the end I performed the procedure myself using a sterilised implanter with the chip preloaded at the factory, delivered in medically sterile packaging.
“The actual process of implanting the chip was a lot less dramatic than many people would think. It healed quickly and it’s actually almost impossible to find the implant site on my arm now.”
Although people like Jonathan are making futuristic scenarios into reality, biometrics has its critics. They say the technology is still a long way from being foolproof, and with a bit of know-how biometrics systems can be bypassed.
“While biometrics can replace most standard security products, they normally require a fixed location and may not necessarily be able to replace them all,” says Neville, who also heads the National Electronic Security Special Interest Group of the Australian Security Industry Association Ltd.
“Other home automation items can be activated by Internet access, timer or even mobile phone interaction. A combination of all of these systems is probably the most effective.”
British software security company KeCrypt, which provides electronic identity validation through its patented biometric signature technology, has produced a white paper on biometrics that outlines the positives and negatives of the technology.
“With an ever-increasing awareness of security and identity theft, there is a need to have a method to identify individuals uniquely and accurately,” the report says.
“Biometrics is seen as a technology to provide such accurate identification.
“But overall there is no one biometric suitable for all applications, and the wider the user group the more difficult the problem becomes.
“In terms of the number of products available, fingerprints must be considered as the leading biometric. However, due to criminal justice implications, fingerprints have certain connotations that make some users wary.
“Also, about 2% of the world population has problems with fingerprint systems as people’s prints have become worn due to manual labour or the patterns are too small to recognise.
“Fingerprints also do not provide a clear intention to authorise because that can be obtained from latent prints left on objects or forced onto readers by unauthorised users.
“More gruesomely, many readers do not check for a live finger.”
Although the commercial adoption of biometrics is relatively new there are several successful biometric projects, KeCrypt says.
“Trials clearly test the performance of the biometric against the original objectives and, most importantly, establish user acceptance.
“If the right biometric is used and introduced properly then users respond well to the benefits.”
Neville says it is important for installers not to lose sight of the primary function of a security system when combining biometrics and home automation.
“As most biometric systems require the reading of a body part via a camera or mirror, which must be kept clean and adjusted, the design of the product and the location of the scanners is of the utmost importance in relation to continuous reliability.
“The more finely matched the biometric type – and therefore the more secure – the more important it is to design the system correctly and maintain for reliability.
“External readers should not be exposed to the elements and must be in a weatherproof housing.”
“The most important thing is that the system still needs to be an Australian Standards approved intruder alarm system that adheres to AS/NZS2201.1:2007. This means the alarm panel must be installed in the protected area in a tamper-proof metal container.
“Further, all wiring to points such as code pads or biometric readers should be monitored for tampering – physically and electronically.
“To add security to a home automation system may not provide the level of security required for the risk. Interfacing a security system with a home automation system, and using biometrics for ease of control, makes more sense.”
-
ADVERTISEMENT
-
ADVERTISEMENT

